Akamai has recently published a new cybersecurity threat advisory through its Prolexic Security Engineering & Research Team (PLXsert). The advisory warns of an increasing use of the outdated Routing Information Protocol version one (RIPv1) for reflection and amplification attacks.
You may already be familiar with the term of DDoS or Distributed Denial of Service. You may, personally, have encountered inaccessible servers or websites due to this type of attack. In a nutshell, DDoS happens when multiple compromised systems (network of computers called ‘botnet’) are used to flood the bandwidth or resources of a targeted server(s) or system with traffic. Incoming traffic can flood a targeted system from different sources and therefore can be tricky to stop simply by blocking IPs as it is difficult to distinguish legitimate user traffic from malicious traffic.
So what’s RIPv1?
RIPv1 is a fast and easy way to dynamically share route information via a small, multi-router network. A typical request is sent by a router running RIP when it is first configured or powered on. Any device listening for requests will respond with a list of routes and updates that are sent as broadcasts.
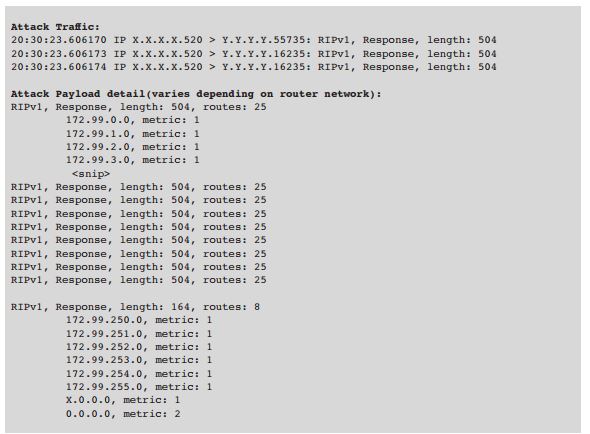
Akamai finds it puzzling that RIPv1 has re-emerged after more than a year of dormancy. The first version of RIP protocol was introduced in 1988, more than 25 years ago under RFC1058. It’s obvious that attackers are exploiting their familiarity with this presumed abandoned DDoS reflection vector. Leveraging the behaviour of RIPv1 to launch a DDoS reflection attack is apparently quite simple for an attacker. The attacker can easily send a normal broadcast query with a malicious query as a unicast request, directly to the reflector. The IP can then be spoofed to match the intended attack target.

With a typical payload size of just 24 bytes, attackers can flood a target with just a small request. Therefore, attackers prefer routers with large amount of routes in the RIPv1 database.
The PLXsert team studied an actual attack against an Akamai customer that happened on 16 May 2015. Data showed that devices leveraged for the RIP reflection attack were likely not using enterprise-grade routing hardware. The team warns that RIPv1 is working as designed and malicious parties will continue to exploit this method as it is fast and easy.
To mitigate this threat, Akamai advises a switch to RIPv2 or later, to enable authentication. It is also advisable to use an access control list (ACL) to restrict User Datagram Protocol (UDP) source port 520 from the internet.
Akamai continues to monitor ongoing campaigns using RIPv1 to launch DDoS reflection attacks.
Want to read more about threats and mitigation techniques? Download a free copy of the threat advisory at www.stateofinternet.com.








