Some 39 apps in Apple’s China App Store including high profile IM platform WeChat were discovered to be infected with malicious code. Apple has acknowledged the problem and began removing the malware-infected apps from the App Store. Some apps are also available in other countries, although authored in China.
So, this is what happened. Developers were unknowingly using counterfeit version of Xcode, Apple’s development software kit, downloaded from alternative sources outside of Apple’s servers.
Counterfeit Xcode, what?
Hackers developed a version of Xcode tools which security experts have dubbed “XcodeGhost” – that would inject malicious code into otherwise legitimate apps. As this code is deeply hidden, it is difficult for iOS users or developers to be aware of any infection.
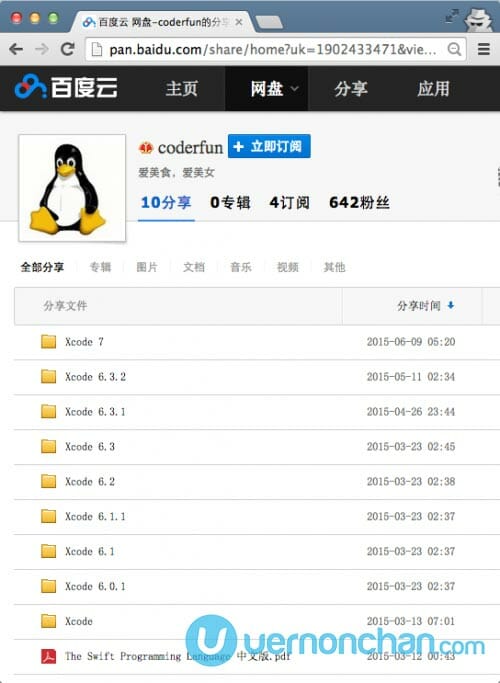
The compromised Xcode software was shared via Baidu’s cloud storage site, promising a faster alternative to the official Apple channel.
Unsuspecting China developers then used the infected development kit to develop and compile their apps before submission to the App Store.
Given Apple’s stringent app review process and policies, it is rather surprising that these apps slipped through Apple’s filters. Apple’s Gatekeeper technology prevents non-App Store and unsigned versions of its apps from being installed on devices. As revealed by TechCrunch, some developers may have chosen to ignore Gatekeeper warnings and proceeded to install and use the compromised software.
Apple has since issued an official statement on the issue:
“Apple takes security very seriously and iOS is designed to be reliable and secure from the moment you turn on your device. We offer developers the industry’s most advanced tools to create great apps. A fake version of one of these tools was posted by untrusted sources which may compromise user security from apps that are created with this counterfeit tool. To protect our customers, we’ve removed the apps from the App Store that we know have been created with this counterfeit software and we are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps.”
There has been conflicting reports of how many apps were infected in total but numbers could run into the hundreds. Apple has not commented on the actual numbers. Apple’s Phil Schiller told Sina website that there has been no reported cases where malicious apps transmitted any user data.
One of the largest IM platforms – TenCent’s WeChat, with over 500 million users, was the most high profile app affected by XcodeGhost.
If you’re using WeChat on your iOS device, it is highly recommended that you delete that app if it isn’t the latest version 6.2.6. Only version 6.2.5 for iOS would have been infected.
TenCent issued an official statement on its blog, acknowledging the issue and quickly patching the flaw. The China-based company announced that there has not been any reports of theft or leakage of users’ information based on preliminary investigations.
A security flaw, caused by an external malware, was recently discovered affecting iOS users only on WeChat version 6.2.5. This flaw has been repaired and will not affect users who install or upgrade WeChat version 6.2.6 or greater, currently available on the iOS App Store. Here are some important points about the situation.
1. The flaw, described in recent media reports, only affects WeChat v6.2.5 for iOS. Newer versions of WeChat (versions 6.2.6 or greater) are not affected.
2. A preliminary investigation into the flaw has revealed that there has been no theft and leakage of users’ information or money, but the WeChat team will continue to closely monitor the situation.
3. The WeChat tech team has extensive experience combating attempts to hack our systems. Once the security flaw was discovered, the team immediately took steps to secure against any theft of user information.
4. Users who encounter any issues can contact the team by leaving feedback in the “WeChat Team” WeChat account.
So how does an infected app affect a user?
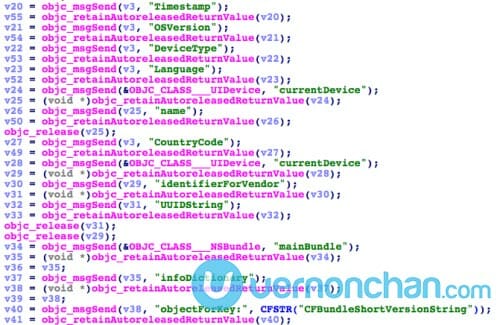
The malicious code in infected apps collects user information like current time, current infected app’s name, app bundle identifier, current device name and type, current system language and country, current device UUID and network type. This information can then be uploaded to command and control (C2) servers.
Check out Palo Alto Networks’ post on how the malicious code in XcodeGhost works and how it attacks a host.
Click here for an updated compiled list of known infected iOS apps.
Source: 9to5Mac, TechCrunch, PaloAltoNetworks, Lookout.com